はじめに
サイトの改竄などの被害が相次いでおり、ついこの前にもニュースで流れていました。
この記事ではサイトの改竄を検知が出来る Tripwire の設定と、また Tripwire のレポートを Slack のインテグレーションを使って受け取る方法についても紹介します。
ここでの構成例
Webサーバー:さくらのVPS(OS:Ubuntu 20.04)
メールサーバー:さくらのメールボックス
flowchart LR
subgraph "さくらのVPS(Webサーバー)"
A[Tripwire] -->|"sendmail"| B[Postfix]
end
subgraph "さくらのメールボックス(メールサーバー)"
B -->|"SMTP/SASL(587)"| C[SMTPサーバー]
end
C -->|"SMTP(25)"| D[Slackインテグレーション]
DNS例
Webサーバーのドメイン: example.com
Slackインテグレーションのメールアドレス: tripwire@example.slack.com
Postfixのインストール + 設定を変更
apt install postfix
vim /etc/postfix/main.cfrelayhost = [mail.example.com]:587
smtp_sasl_auth_enable = yes
smtp_sasl_password_maps = hash:/etc/postfix/relay_password
smtp_sasl_security_options = noanonymousvim /etc/postfix/master.cfsubmission inet n - y - - smtpd
-o smtpd_sasl_auth_enable=yes
-o smtpd_recipient_restrictions=permit_sasl_authenticated,rejectリレー先(さくらのメールサーバー)のユーザー名とパスワードを追記します。
vim /etc/postfix/relay_password[mail.example.com]:587 username:passwordpostmap /etc/postfix/relay_password
systemctl restart postfixTripwireのインストール
apt install tripwireサイトキーパスフレーズ と ローカールキーパスフレーズ を決めるので、忘れないように控えておきます。
設定ファイルの変更
cp /etc/tripwire/twcfg.txt /etc/tripwire/twcfg.txt.org
vim /etc/tripwire/twcfg.txtROOT =/usr/sbin
POLFILE =/etc/tripwire/tw.pol
DBFILE =/var/lib/tripwire/$(HOSTNAME).twd
REPORTFILE =/var/lib/tripwire/report/$(HOSTNAME)-$(DATE).twr
SITEKEYFILE =/etc/tripwire/site.key
LOCALKEYFILE =/etc/tripwire/$(HOSTNAME)-local.key
EDITOR =/usr/bin/editor
LATEPROMPTING =false
LOOSEDIRECTORYCHECKING =true
MAILNOVIOLATIONS =false
EMAILREPORTLEVEL =3
REPORTLEVEL =4
SYSLOGREPORTING =true
MAILMETHOD =SENDMAIL
MAILPROGRAM =/usr/sbin/sendmail -oi -t -f tripwire@example.com
TEMPDIRECTORY =/tmp暗号化
twadmin -m F -c /etc/tripwire/tw.cfg -S /etc/tripwire/site.key /etc/tripwire/twcfg.txtポリシーファイル(twpol.txt)
DocumentRoot( /var/www/html )に対して監視をして、 LaravelのSessionファイルは除外する 場合です。
@@section GLOBAL
# Tripwireに関連するパスを定数として指定
TWBIN = /usr/sbin;
TWETC = /etc/tripwire;
TWVAR = /var/lib/tripwire;
@@section FS
# プロパティを定数として指定
SEC_BIN = $(ReadOnly);
SEC_CONFIG = $(Dynamic);
# 重要度を定数として指定
SEC_LOW = 33;
SEC_MED = 66;
SEC_HI = 100;
(
rulename = "DocumentRoot",
emailto = "example@fourier.slack.com",
severity = $(SEC_MED),
recurse = true
)
{
/var/www/html -> $(SEC_CONFIG);
!/var/www/html/example.com/shared/storage/framwork/sessions;
}暗号化
twadmin -m P -c /etc/tripwire/tw.cfg -p /etc/tripwire/tw.pol -S /etc/tripwire/site.key /etc/tripwire/twpol.txt差分DBの初期化
tripwire --initTripwireの実行
tripwire --check --email-report
tripwire -m -c -M #(↑のシノニム)
--email-report / -M を付けると、ファイルに変更があった場合(= Total violations foundが1以上の場合)にメールを送信されます。
root@XXXXXX:/var/www/html# tripwire -m c
Parsing policy file: /etc/tripwire/tw.pol
*** Processing Unix File System ***
Performing integrity check...
Wrote report file: /var/lib/tripwire/report/XXXXXX-20220630-184642.twr
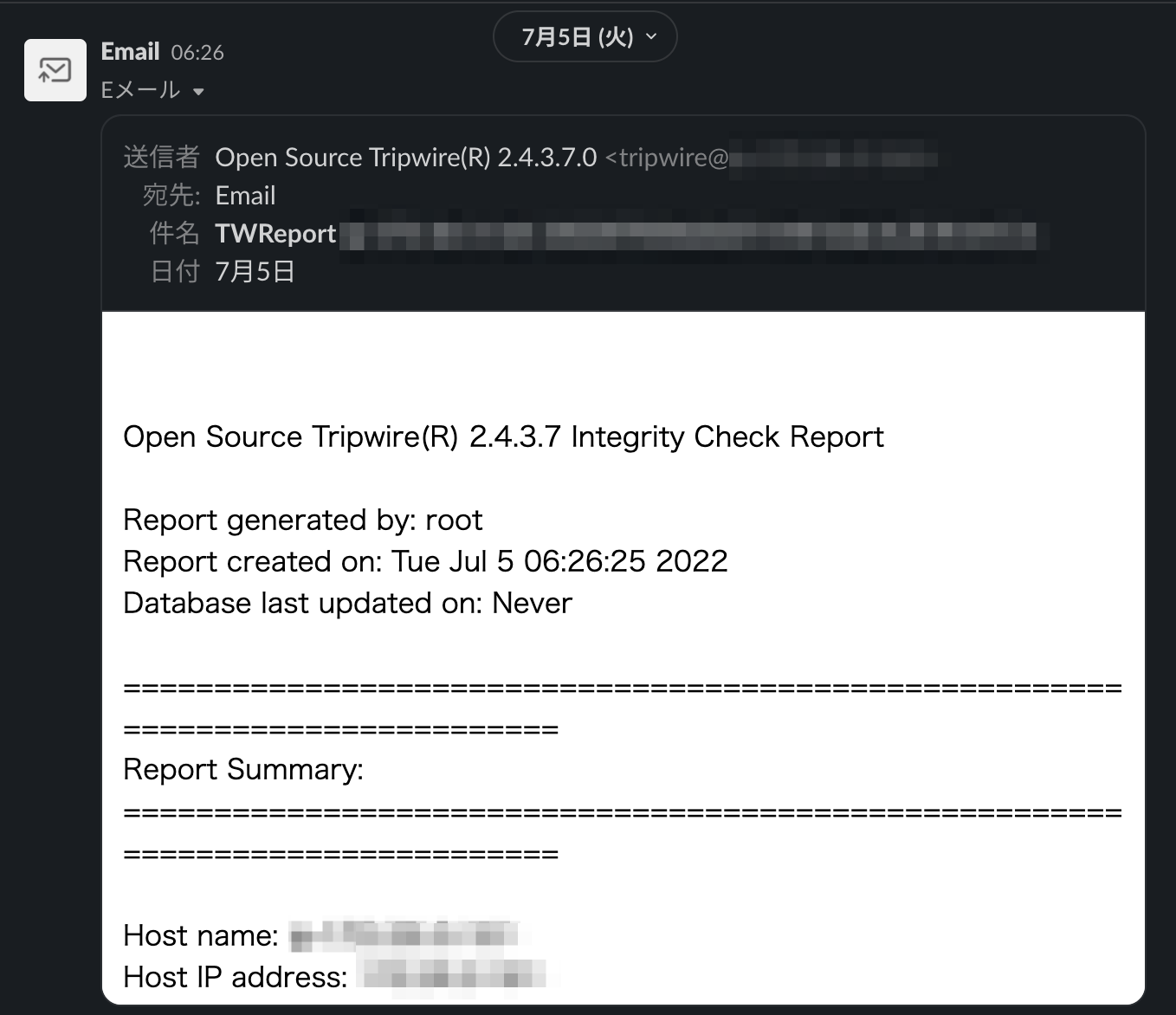
Open Source Tripwire(R) 2.4.3.7 Integrity Check Report
Report generated by: root
Report created on: Thu Jun 30 18:46:42 2022
Database last updated on: Never
===============================================================================
Report Summary:
===============================================================================
Host name: XXXXXX
Host IP address: XXXXXX
Host ID: None
Policy file used: /etc/tripwire/tw.pol
Configuration file used: /etc/tripwire/tw.cfg
Database file used: /var/lib/tripwire/XXXXXX.twd
Command line used: tripwire -m c
===============================================================================
Rule Summary:
===============================================================================
-------------------------------------------------------------------------------
Section: Unix File System
-------------------------------------------------------------------------------
Rule Name Severity Level Added Removed Modified
--------- -------------- ----- ------- --------
DocumentRoot 66 0 0 0
(/var/www/html)
Total objects scanned: 39893
Total violations found: 0
===============================================================================
Object Summary:
===============================================================================
-------------------------------------------------------------------------------
# Section: Unix File System
-------------------------------------------------------------------------------
No violations.
===============================================================================
Error Report:
===============================================================================
No Errors
-------------------------------------------------------------------------------
*** End of report ***
Open Source Tripwire 2.4 Portions copyright 2000-2018 Tripwire, Inc. Tripwire is a registered
trademark of Tripwire, Inc. This software comes with ABSOLUTELY NO WARRANTY;
for details use --version. This is free software which may be redistributed
or modified only under certain conditions; see COPYING for details.
All rights reserved.
Integrity check complete.例えばなんらかのファイルを変更すると・・・
root@XXXXXX:/var/www/html# touch index2.html
root@XXXXXX:/var/www/html# tripwire -m c
Parsing policy file: /etc/tripwire/tw.pol
*** Processing Unix File System ***
Performing integrity check...
Wrote report file: /var/lib/tripwire/report/XXXXXX-20220630-184729.twr
Open Source Tripwire(R) 2.4.3.7 Integrity Check Report
Report generated by: root
Report created on: Thu Jun 30 18:47:29 2022
Database last updated on: Never
===============================================================================
Report Summary:
===============================================================================
Host name: XXXXXX
Host IP address: XXXXXX
Host ID: None
Policy file used: /etc/tripwire/tw.pol
Configuration file used: /etc/tripwire/tw.cfg
Database file used: /var/lib/tripwire/XXXXXX.twd
Command line used: tripwire -m c
===============================================================================
Rule Summary:
===============================================================================
-------------------------------------------------------------------------------
Section: Unix File System
-------------------------------------------------------------------------------
Rule Name Severity Level Added Removed Modified
--------- -------------- ----- ------- --------
* DocumentRoot 66 0 0 1
(/var/www/html)
Total objects scanned: 39893
Total violations found: 1 // 0 を 1 に変更
===============================================================================
Object Summary:
===============================================================================
-------------------------------------------------------------------------------
# Section: Unix File System
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
Rule Name: SamplePolicy (/var/www/html)
Severity Level: 66
-------------------------------------------------------------------------------
Modified:
"/var/www/html/index2.html"
===============================================================================
Error Report:
===============================================================================
No Errors
-------------------------------------------------------------------------------
*** End of report ***
Open Source Tripwire 2.4 Portions copyright 2000-2018 Tripwire, Inc. Tripwire is a registered
trademark of Tripwire, Inc. This software comes with ABSOLUTELY NO WARRANTY;
for details use --version. This is free software which may be redistributed
or modified only under certain conditions; see COPYING for details.
All rights reserved.
Integrity check complete.メールが送信されます。
cronの設定
UbuntuにインストールするとCronが入れているので、それを編集します。
vim /etc/cron.daily/tripwire
+ の部分を追記
#!/bin/sh -e
tripwire=/usr/sbin/tripwire
+ LOCALPASS='password' # ローカルパスフレーズ
[ -x $tripwire ] || exit 0
umask 027
$tripwire --check --quiet --email-report
+ $tripwire --init -P $LOCALPASS毎回初期化をすることによって、以前検出された変更点は検出されなくなります。
まとめ
サイトの改竄を検知が出来る Tripwire を使うことにより、例え改竄をされても検知して早急に対応することにより被害を最小限の抑えることが出来ます。
改竄させないような仕組みを作ることがまず重要ですが、さらに最小限に抑える仕組みを組み込むことが次に重要になると思います。
